HIPAA, or the Health Insurance Portability and Accountability Act, is a set of regulations that govern the use, storage, and disclosure of protected health information (PHI). All ABA service providers must adhere to HIPAA regulations when using electronic data collection systems for goal tracking. Failure to comply with these regulations can result in hefty fines and a negative impact on the reputation of the service provider.
Overview of HIPAA
HIPAA was enacted in 1996 to protect the privacy and security of individuals' health information. The law sets national standards for the use and disclosure of PHI by healthcare providers, health plans, and healthcare clearinghouses. HIPAA also provides individuals with certain rights related to their health information, such as the right to access and obtain copies of their own health records, and the right to request corrections to their health information. With the rise of electronic health records and data collection systems, it is more important than ever to protect the privacy and security of individuals’ health information. This not only protects individuals’ rights, but also helps to build trust between healthcare providers and patients.
Key HIPAA Requirements for ABA and Developmental Therapy Service Providers
Service providers must comply with several HIPAA regulations, including:
- The Privacy Rule, which requires that PHI be kept confidential and only disclosed when necessary for treatment, payment, or healthcare operations.
- The Security Rule, which mandates that all electronic PHI be kept secure through data encryption, access controls, and regular security audits.
- The Breach Notification Rule, which requires that service providers notify affected individuals, the Department of Health and Human Services, and in certain cases, the media, in the event of a data breach.
It is important for service providers to have a thorough understanding of these regulations and to implement policies and procedures to ensure compliance. This may include training staff on HIPAA regulations, implementing secure electronic data collection systems, and regularly reviewing and updating security measures. Additionally, service providers should have a plan in place for responding to potential data breaches. This plan should include steps for containing the breach, notifying affected individuals and authorities, and conducting a thorough investigation to determine the cause of the breach and prevent future incidents. By implementing these measures, service providers can ensure that they are in compliance with HIPAA regulations and are providing the highest level of privacy and security for their clients’ health information.
Implementing Secure Data Collection Practices in Motivity
Once your organization starts using Motivity, it is important to implement secure data collection and storage practices. These practices not only ensure compliance with HIPAA regulations but also safeguard sensitive patient information.
Access Controls
Access controls should be implemented to ensure that only authorized individuals have access to PHI. This includes limiting access to the minimum necessary information needed to perform job duties. Access controls are managed at the permissions level in Motivity.
Limit Owner role to minimum necessary individuals. The Owner role can see and change everything. Restrict it to only a few key people, such as company owners and/or critical personnel that need to manage access and permissions for all users.
Use Roles, Permissions, and Teams to Limit PHI access. Rather than having your staff be able to view all data for all learners, you can assign them to specific learners’ Teams, then use the “if on team” permission in their assigned Roles to prevent them from accessing learners not on their team.
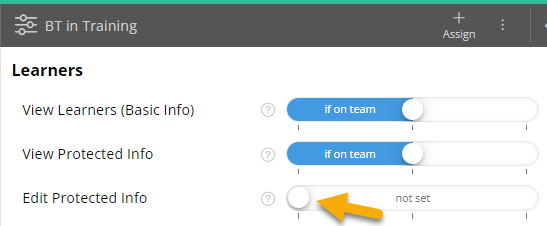
It is also important to regularly review and update roles, permissions, and team assignments to ensure that they are still effective. This can include removing specific team membership or roles from staff who no longer require it.
De-Identification
Use the “Alias” field to reduce exposure to patient identifiers. The Alias field is intended to be used as a way to reference a learner without using identifiers. It can be edited in the Learner Profile. Alias is displayed in numerous places throughout the system (such as in the Learner cards when viewing all Learners), whereas the learner’s name is only specified in a limited set of places (such as the Profile or Notes/Reports that require it). By avoiding identifiers in the Alias, you can minimize unnecessary exposure. Example: suppose an unauthorized individual gains access to a screenshot of a Motivity displaying a list of learners. If de-identified Aliases are used, it is unlikely to be considered a HIPAA breach. As such, your organization should NOT use a learners’ first name, last name, or even initials for the Alias, because those are all considered identifiers. Instead, choose a randomly assigned string of letters and numbers, or an arbitrary pseudonym, e.g.:
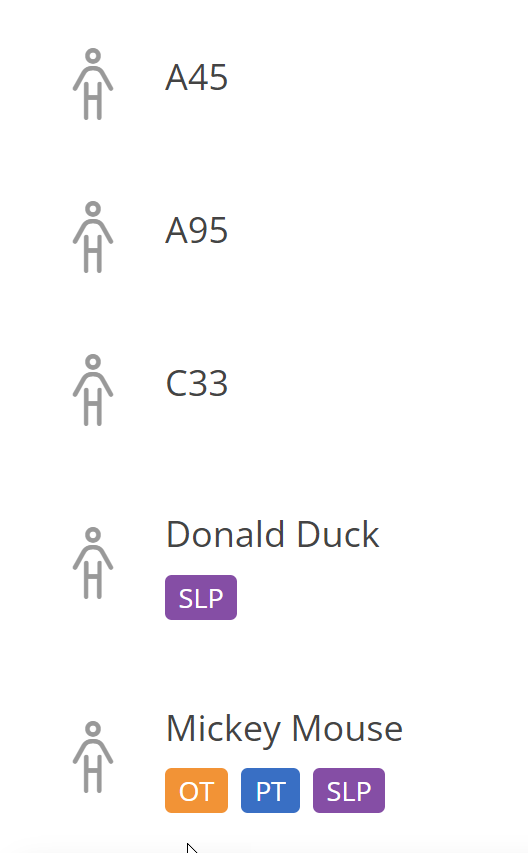
Securing Devices
Train your staff to ensure that every device used to access Motivity is protected. Follow HIPAA best practices. The operating system should be configured to require a password or passcode to open the device after it’s gone to sleep or not been used in a while. Maintain a policy that your staff should not share or re-use logins or passwords, and that passwords should be at least 8 characters in length and include upper and lower case letters, numbers and special characters.
Ensure that any device used to access Motivity is hardened against security threats, e.g. has regular system updates and appropriate antivirus and anti-malware software as recommended for that device class.
Regular Security Audits and Risk Assessments
Service providers should perform regular security audits and risk assessments to identify potential vulnerabilities and to ensure that all security measures are up-to-date and effective. This can include reviewing policies and procedures, conducting vulnerability scans, and testing the effectiveness of access controls. Any identified vulnerabilities should be addressed promptly to minimize the risk of a data breach. This can include implementing additional security measures or updating existing ones.
Developing a Data Breach Response Plan
Despite best efforts, data breaches can still occur. Service providers should develop and implement a data breach response plan to ensure a quick and effective response in the event of a breach. The plan should include steps such as identifying the cause and extent of the breach, notifying affected individuals and the appropriate regulatory authorities, and taking steps to prevent future breaches. It is also important to regularly review and update the data breach response plan to ensure that it is still effective. This can include conducting tabletop exercises to test the plan and identifying areas for improvement. By implementing secure data collection and storage practices, service providers can protect sensitive patient information and ensure compliance with HIPAA regulations. Regularly reviewing and updating these practices can help to identify potential vulnerabilities and prevent data breaches.
Ensuring Staff Training and Awareness
Service providers must ensure that all staff members who handle PHI receive HIPAA training and are aware of their obligations to maintain the confidentiality and security of client information.
HIPAA Training for Service Providers
HIPAA training is essential for all staff members who handle PHI, including service providers. HIPAA training should cover key HIPAA regulations, including the Privacy, Security, and Breach Notification Rules. It should also cover the best practices for handling PHI, such as the importance of encryption and access controls, and the steps to take in the event of a data breach.
During the training, staff members should learn about the types of PHI that are protected under HIPAA, including medical records, billing information, and other personal identifying information. They should also learn about the consequences of non-compliance with HIPAA regulations, which can include fines, legal action, and damage to the reputation of the service provider.
Ongoing Education and Updates on HIPAA Regulations
HIPAA regulations are subject to change, and service providers must stay up-to-date on any changes to ensure ongoing compliance. Service providers should provide ongoing education and updates to staff members on HIPAA regulations and best practices for maintaining the confidentiality and security of client information.
Service providers can provide ongoing education through regular staff meetings, online training modules, and other educational resources. They should also encourage staff members to report any potential HIPAA violations or security breaches, and provide a clear reporting process for staff members to follow.
By ensuring that all staff members are trained and aware of their obligations under HIPAA, service providers can help to protect the privacy and security of client information, and avoid potential legal and reputational risks.


